LinkedIn's 2.5-Factor Authentication
17 Jul 2013Almost a year after its password database was hacked, LinkedIn finally enabled two-factor authentication. Unlike single factor authentication that requires only something a user knows (a password), two-factor authentication also requires something the user possesses. This can be a cell phone that will receive an additional piece of information to prove that you are, in fact, you. LinkedIn's two-factor authentication uses your password and a randomly-generated code that is sent to your cell phone, which is common practice and used by companies like Google, Facebook, and Dropbox. The way LinkedIn presents its two-factor authentication is where the company really shines... And not in a good way!
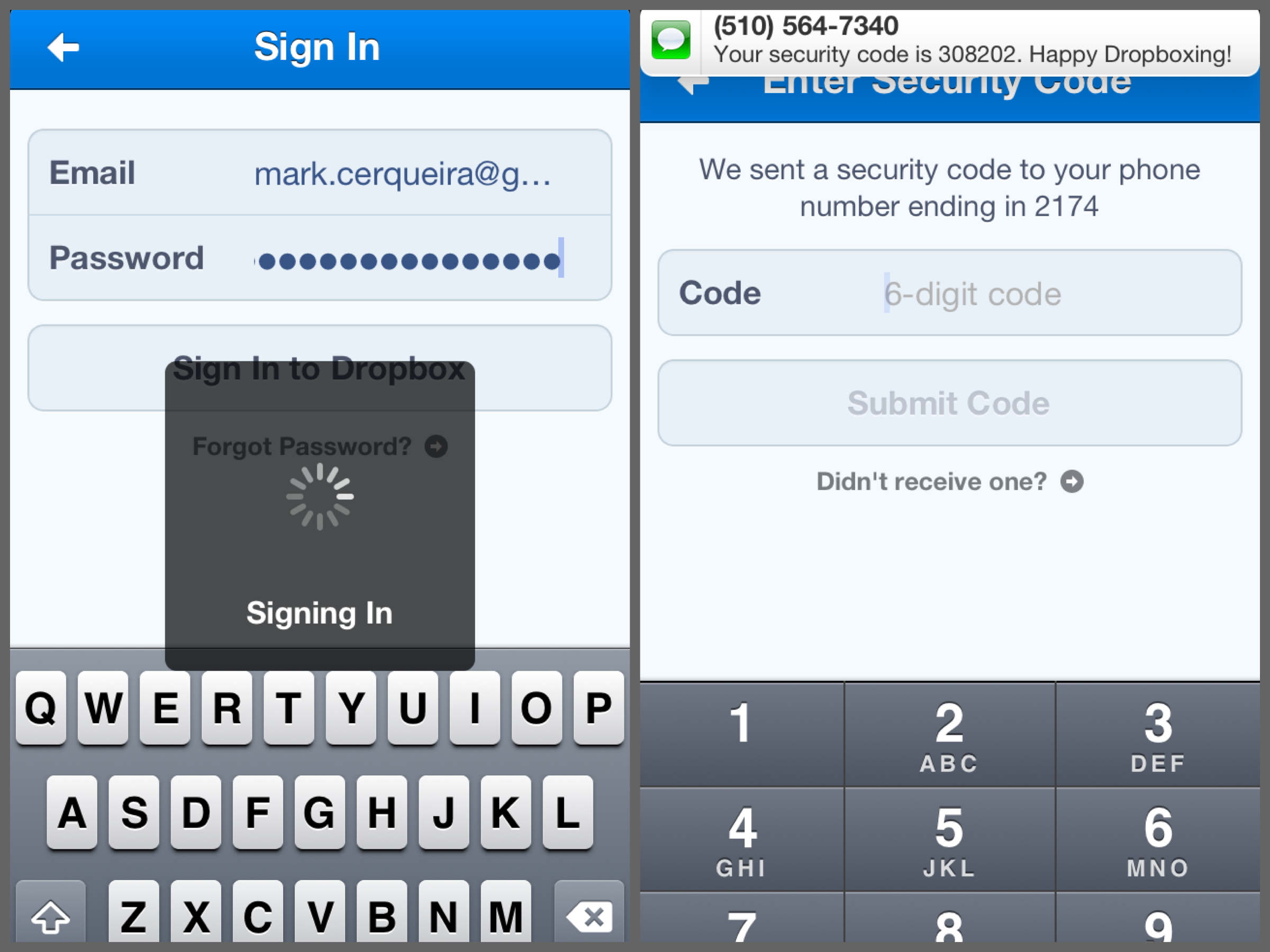
2-factor authentication on the Dropbox iOS app.
First, let’s look at how Facebook (version 6.3) and Dropbox (version 2.3) handle two-factor authentication on iOS. You start by entering your email and password. If those are correct, you’re past the first stage of authentication. You are informed that your phone will be sent a code (the second piece of authentication), and then you’re brought to a screen with a number pad. You receive a text message with the promised code and are able to input the code. After passing two methods of authentication, you’re in!
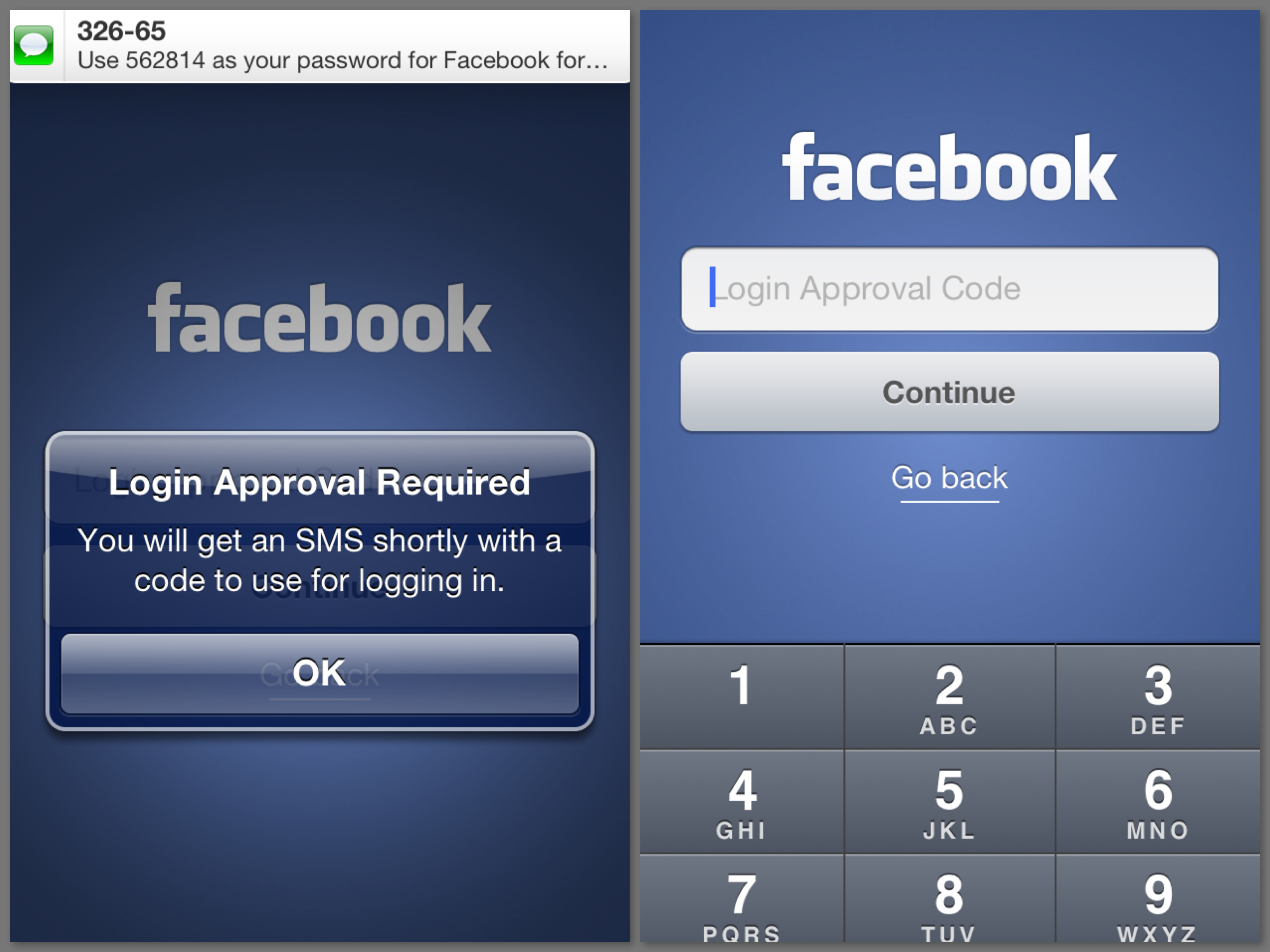
2-factor authentication on the Facebook iOS app. Note the inconsistency with which Facebook refers to the security code.
Everything is simple and clean, aside from Facebook being inconsistent in what it calls the security code: the app states that you will get a code via SMS, then calls that code a password in the SMS, and then asks for a Login Approval Code in the app. Dropbox keeps things much more consistent: stating a security code will be sent to your phone, calling that code a security code in its text message, and then asking for a 6-digit code in the app.
Now, let’s take a look at LinkedIn (version 6.1). Everything starts out similarly. You enter your email and password, and if those are correct, you proceed to the next step of authentication. It looks like this:
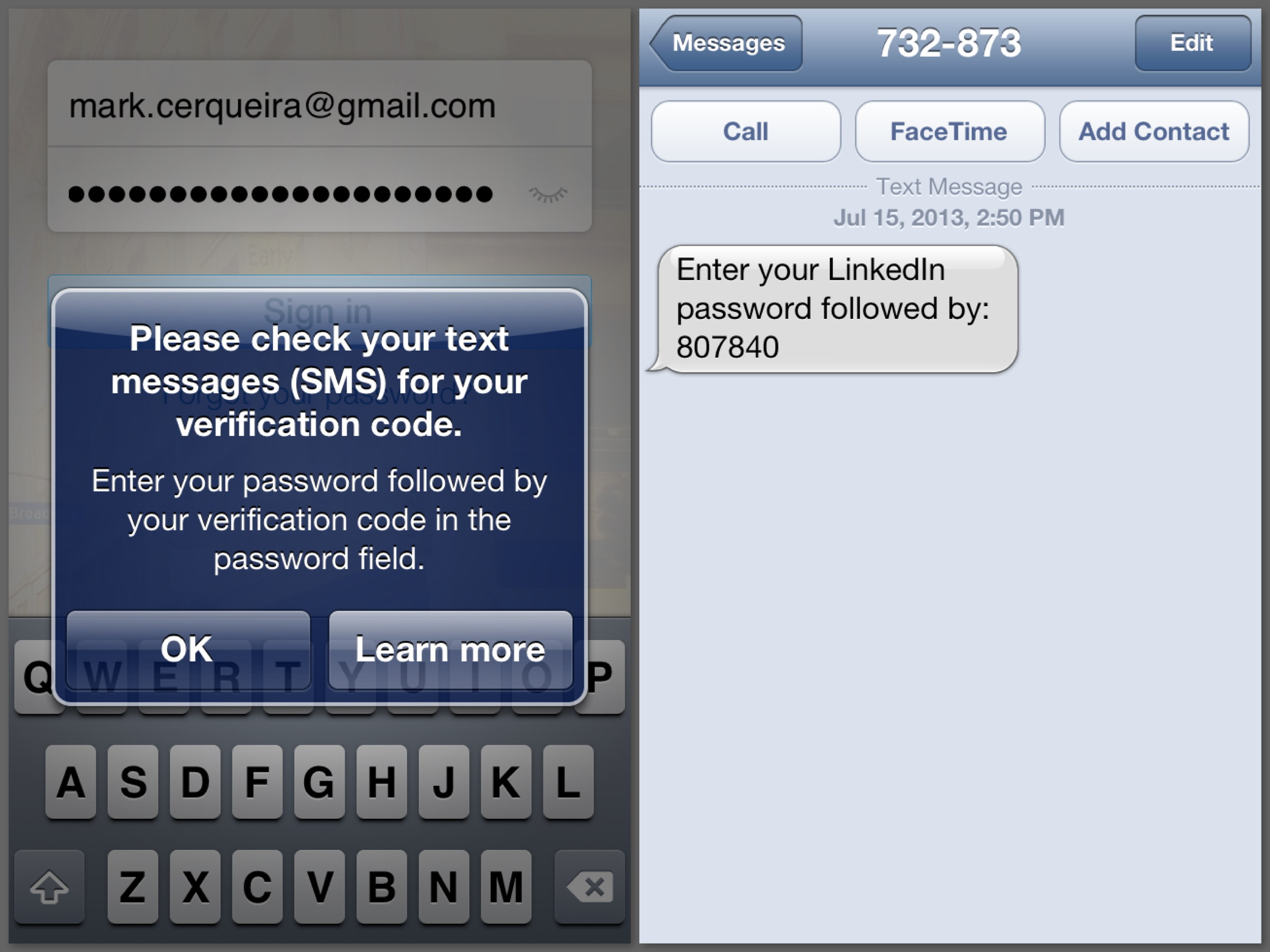
Wait... I have to do what!?
Why would they have me append my security code to my password – in the same field!? Their iOS team forgoes implementing a new screen, the server team picks up the slack and separates the security code from the password, and the user is left dumbfounded as to why LinkedIn took an entire year since their password leak to send two-factor authentication to an alternate realm of terrible user experiences.
Well, at least the instructions in the app and the text message are consistent; let’s just follow the instructions and be finished with this. I dismiss the UIAlertView by hitting the OK button, the text message comes in with the code, I switch to the numeric/symbol mode of the keyboard of which I will only use the numbers, and I carefully input the first number. Lo and behold, my password that was formerly there is gone!
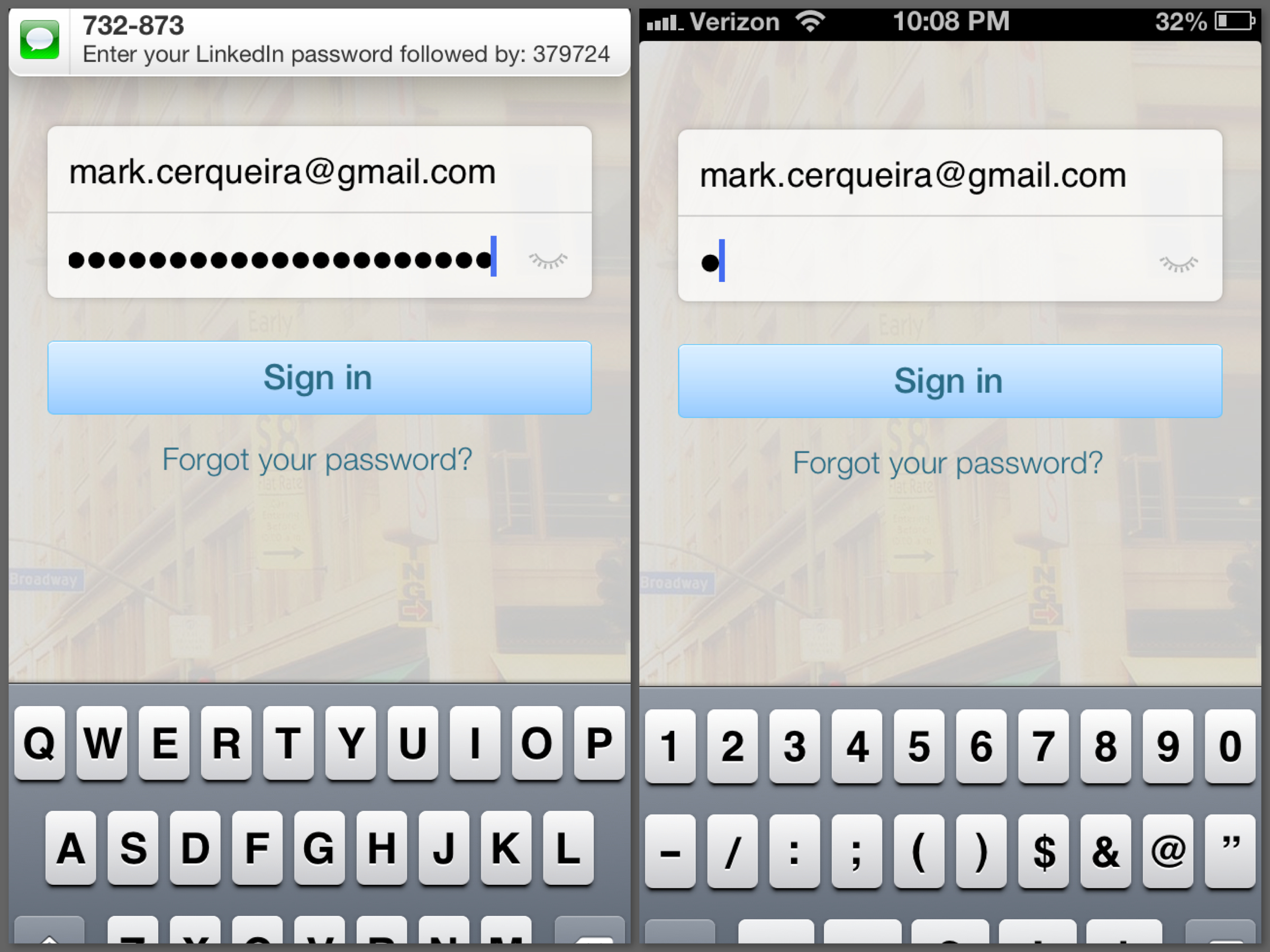
Just when you thought things couldn't get worse...
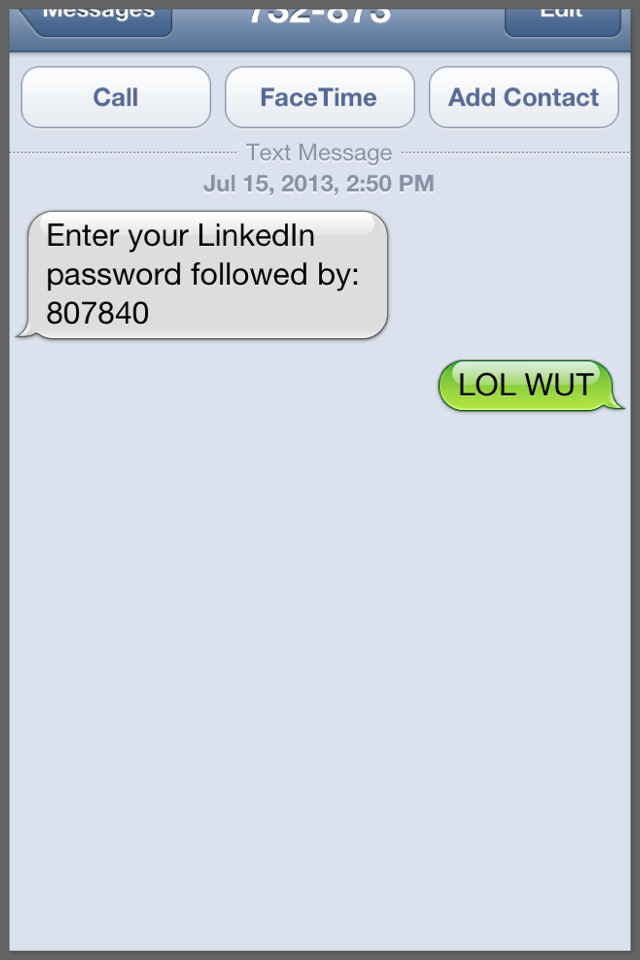
That’s right. When the text message says Enter your LinkedIn password followed by: 123456, whether by accident or design, it literally means type your password in AGAIN, but add these 6 digits to the end. Perhaps this is some new hybrid of 2-factor authentication – enter your password, and then enter your password again, but add a security code to the end. It’s silly. You don’t need to sacrifice convenience for added security. So for now, I’ll just assume this is a big joke on LinkedIn’s part…